Web application security is becoming increasingly important in Nigeria, where rapid digitization has pushed more businesses, government services, fintech platforms, and e-commerce systems online. Unfortunately, many of these systems are being deployed or maintained without strong security controls, making them vulnerable to some of the most common attack vectors.
This article explores the most common web attacks in Nigeria and agents that carry out these attacks (actors), why they are widespread, and what we can do to defend our systems.
Understanding OWASP in the Nigerian Context
OWASP (Open Web Application Security Project) OWASP Top 10 provides a widely used list of the most critical web application security risks. These vulnerabilities appear everywhere globally but certain economic and technological conditions in Nigeria make some of them disproportionately common.
The following factors contribute to making web applications easy targets for attacks :
-
poor patching practices,
-
use of outdated or pirated software,
-
weak authentication policies,
-
rapid growth of online services,
-
limited cybersecurity budgets, and
- lack of trained security personnel

1. Injection Attacks (SQLi, Command Injection, etc.)
This type of attack where a hacker tricks your website into giving them access to your database.It is one of the most prevalent attacks in Nigeria. Since many organizations deploy database-driven websites without properly checking user inputs, making them vulnerable to SQL injection and other forms of injection. Given the rise of fintech and e-commerce platforms in Nigeria, this category is especially dangerous.
Why injection is so common in Nigeria
-
Widespread use of old PHP/MySQL sites
-
CMS platforms using insecure plugins or custom themes
-
Developers relying on raw queries instead of ORMs
-
Limited security testing before product release
Real-world impact
Attackers use SQLi to:
-
Dump databases (View all data in a database)
-
Take over admin accounts
-
Install backdoors
-
Steal sensitive customer information
2. Broken Authentication & Session Management
This happens when a website’s login system is weak or poorly implemented giving rise to issues such as those listed below. Credential attacks are extremely common across Nigerian websites, especially those built on WordPress, Laravel, and older PHP stacks.
Common issues
-
Allowing weak or reused passwords which may leaked from the users accounts with other websites
-
Admin pages exposed publicly
-
No rate-limiting on login attempts
-
Lack of 2-factor authentication
-
Poor session timeout settings
Common attack types
-
Credential stuffing (Trying usernames and password combinations gotten from leaks )
-
Brute-force attacks (trying random entries such as trying all 5 letter words + a number for a system that accept 6 character passwords)
-
Session hijacking
-
Cookie theft and replay
Alot of us are using the same password across multiple platforms, making these attacks remain easy and effective.
3. Cross-Site Scripting (XSS)
An attack where a hacker sneaks malicious scripts into a website so the script runs in the victim’s browser. This can happen through comments, forms, or any user input the site shows back to others. XSS attacks arise when user input is not properly sanitized. They are frequently found in Nigerian CMS sites using outdated or poorly built plugins.
Why XSS persists in local ecosystems
-
Heavy reliance on WordPress without updating plugins frequently.
-
Use of pirated/nulled themes (which may already contain vulnerabilities)
-
Lack of HTML/JS sanitization in custom forms
What attackers do with XSS
-
Steal session cookies
-
Inject fake login pages
-
Redirect users to phishing or malware sites
-
Deface websites
-
Inject malicious JavaScript (cryptominers, keyloggers, etc.)
4. Using Vulnerable or Outdated Components
Perhaps the single biggest enabler of attacks in Nigeria is the widespread use of:
-
outdated CMS platforms,
-
discontinued themes,
-
unpatched plugins, or
-
cracked/nulled software.
Why this is a major problem
Because many businesses rely on freelancers who deploy sites and never stay to maintain them
-
Developers may use pirated themes/plugins with hidden malware
-
Organizations delay updates because they fear “breaking” something therefore proper vulnerability patching is often ignored.
This leads directly to:
-
Backdoor installations from malicious softwares
-
Site takeovers
-
Massive data breaches
-
Ransomware attacks
-
Silent malware injections
5. Security Misconfiguration
Misconfigurations are everywhere unsecured admin panels, exposed .env files, debug mode left on, public buckets, open ports, etc. These weaknesses often give attackers an immediate foothold without much effort.
Common misconfigurations in Web Applications
-
Exposed phpMyAdmin panels
-
Default database passwords
-
Debug mode ON in production
-
Public S3 or Cloudinary buckets
-
Revealing server headers
-
Incorrect permission settings
-
Firewalls disabled or misconfigured
6. Malware & Ransomware via Web Vulnerabilities
While malware isn’t an OWASP category by itself, the entry point for most malware attacks in Nigeria comes directly from:
-
outdated components
-
injection flaws
-
weak authentication
-
misconfiguration
Attackers commonly deploy
-
ransomware
-
credit card skimmers
-
phishing toolkits
-
cryptominers
Once inside, attackers often sell access to the compromised server or use it for further phishing campaigns.
Why These Attacks Are So Common in Nigeria
Understanding the root causes helps explain why Nigeria sees such high attack frequency:
-
Lack of patching & updates
-
SMEs and agencies often run outdated systems for years.
-
Reliance on cheap or pirated website templates that often come pre-infected.
-
Weak cybersecurity culture. Security is usually an afterthought until after a breach.
-
Rapid digital adoption. Fintech, e-commerce, betting platforms, and online services grow faster than security awareness.
- Lack of professional cybersecurity staff. Many organizations rely on junior developers or non-security professionals to manage servers.
Who carries out these attack ?
Threat actors are individuals, groups, or organizations that carry out malicious activities against digital systems, networks, or users. They are the people behind cyberattacks — the ones who plan, execute, or benefit from them.
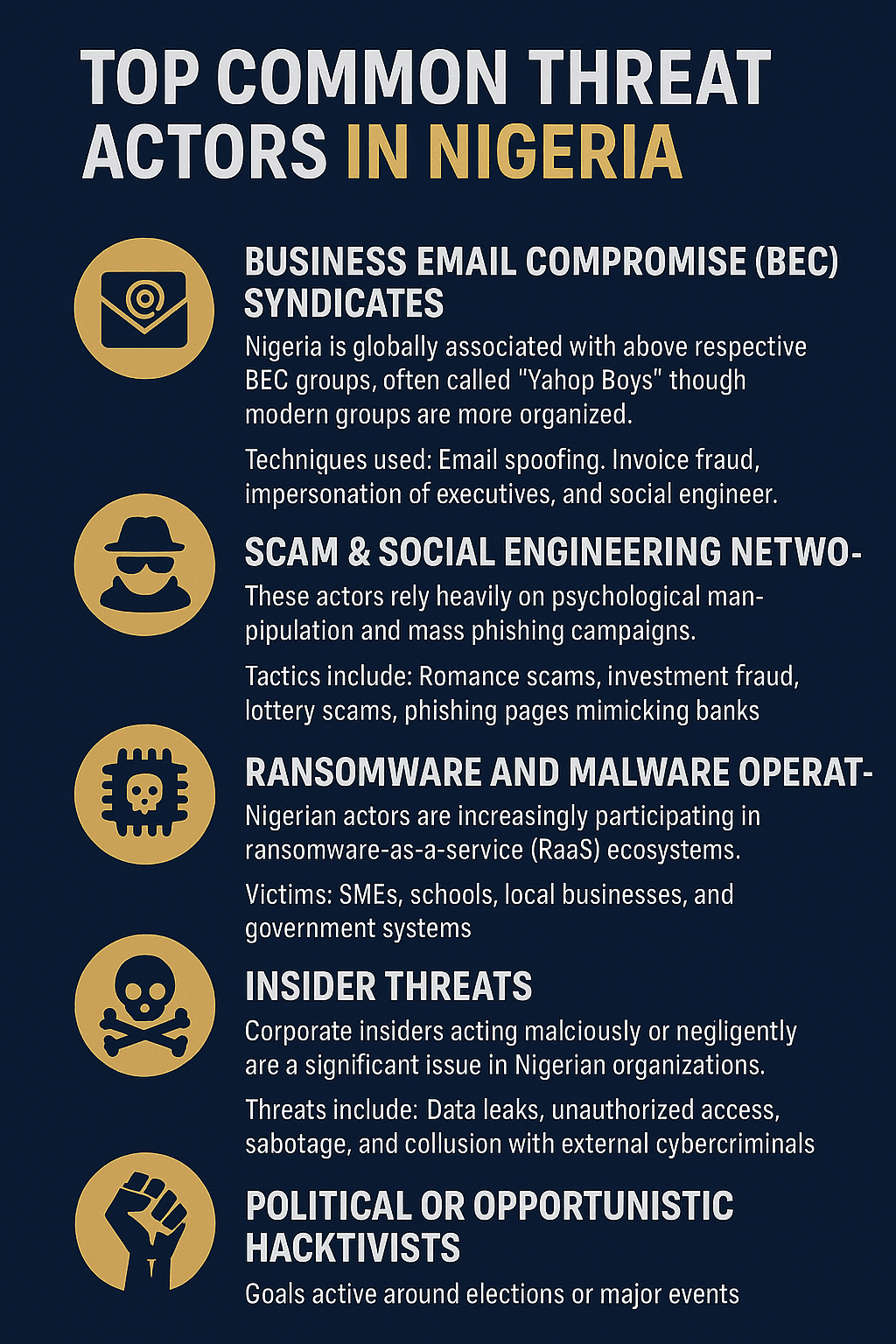
What Threat Actors Do
Threat actors typically:
-
Exploit weaknesses (technical or human)
-
Steal data or money
-
Disrupt services
Common Motivations
Threat actors usually operate for:
-
Financial Gain (e.g., BEC scammers, ransomware groups)
-
Espionage (government-backed actors)
-
Ideology / Activism (hacktivists)
-
Revenge or Malice (insiders or ex-employees)
-
Fun or Challenge (script kiddies)
Examples of Threat Actors
Cybercriminals (scammers, fraud rings, ransomware gangs)
Insider threats (employees abusing access)
Hacktivists (Anonymous-style groups)
Nation-state groups (APT groups)
Script kiddies (low-skill attackers using pre-made tools)
Here are some tips organizations can follow to better protect themselves and their clients:
-
Fix Authentication Issues
-
Enforce strong passwords
-
Rate-limit login attempts
-
Enable 2FA everywhere possible
-
Hide admin login routes
-
-
Prevent Injection
-
Use ORM or parameterized queries
-
Treat all iuser nputs as untrusted
-
Implement server-side validation
-
-
Patch Everything
-
Update themes, plugins, and CMS versions
-
Avoid cracked or nulled extensions
-
Subscribe to vendor security alerts
-
-
Conduct Regular Security Testing
-
Strengthen Developer & Employee Awareness: Human error is still the biggest cybersecurity weakness.
- Training should include:
- Secure coding practices
- How to identify phishing emails
- Password hygiene
- Safe use of corporate devices
- Data handling policies

Comments (0)
No comments yet. Be the first to comment.